PODCAST: Explore the shadowy world of domestic and international surveillance and harassment, drawing connections between government intelligence agencies, law enforcement, and private security firms. They document instances of alleged “gang stalking” or “organized stalking,” a term used to describe systematic harassment and psychological manipulation often targeting individuals, which some victims attribute to corrupt officials or private entities. The sources highlight concerns about accountability and transparency within these powerful institutions, noting a perceived “deep state” that operates with limited oversight and sometimes engages in illegal activities like discrediting journalists or manipulating public perception through disinformation. Several articles discuss the potential for violence stemming from such harassment campaigns, citing cases where individuals who claimed to be “targeted” later committed violent acts. Ultimately, the collection underscores a pervasive skepticism towards official narratives and calls for greater public awareness and investigation into these secretive practices.
The historical instances of state-sanctioned surveillance and harassment significantly inform the current understanding of alleged “gang stalking” phenomena by demonstrating a precedent for similar tactics and motivations, challenging the notion that such claims are purely delusional, and highlighting a systemic lack of oversight and accountability in security and intelligence operations.
Here’s how these historical instances inform the current understanding:
- Established Methods of Covert Harassment: The sources frequently draw parallels between alleged “gang stalking” and well-documented historical “disruption operations” or “psychological terrorism” techniques.
- COINTELPRO: The FBI’s illegal surveillance program, exposed in 1971, involved intimidation of law-abiding Americans and targeting dissident groups, including blackmailing Martin Luther King, Jr., and attempts to pressure him to kill himself. It also involved tactics like slander, blacklisting, and “black bag jobs”. This program’s revelations required activists to steal secret documents to expose the government’s crimes.
- Stasi (Zersetzung): Communist East Germany’s secret police, the Stasi, perfected psychological techniques known as “Zersetzung” (corrosion or undermining) in the 1970s and 1980s. These methods aimed to “switch off” regime opponents by disrupting their private or family lives through subtle acts like moving personal items, opening windows, setting alarms, replacing tea, or even sending vibrators to a target’s wife. The goal was to make victims believe they were “going mad,” with some suffering breakdowns or even killing themselves, ensuring the state could deny responsibility. Such tactics were favored for their deniability and political safety compared to overt persecution.
- CIA’s MKUltra: This secret program involved mind control experiments on Americans, with much of the evidence later destroyed by the CIA. The case of Theodore Kaczynski (“the Unabomber”) is explored, questioning whether his terrorist acts were rooted in the psychological torture he experienced during CIA’s MKUltra experiments, suggesting that his fears of mind control were not delusional in that context.
- Modern Day Disruption Operations: U.S. intelligence agencies and law enforcement continue to use “disruption operations” against suspects or individuals they cannot prosecute, including forms of harassment, infiltration, and psychological manipulation. Reports describe tactics such as overt stalking, libel, “black bag jobs” (breaking into homes to rearrange items or defecate on carpets), and using street-level law enforcement for harassment.
- Plausibility and Credibility of Claims: The existence of these historical and ongoing covert operations provides a basis for accepting that claims of “gang stalking” might not be entirely delusional.
- When a reporter’s article characterizes all online discussion of “gang stalking” as “paranoia” and omits relevant news reports, it raises questions about the article being disinformation or journalistic incompetence.
- Reports of credible individuals, such as a San Diego Medical Director, a technology entrepreneur in Australia, and whistleblowers whose claims of harassment were vindicated in court, lend credibility to the phenomenon beyond mere conspiracy theories.
- The fact that entities like the FBI refuse to comment publicly on “organized stalking,” even when it’s associated with violence, is seen as “revealing”.
- Impunity and Lack of Oversight: The historical record demonstrates a consistent pattern of intelligence and law enforcement agencies operating with minimal accountability and oversight, which facilitates the perpetration of such secret harassment.
- Even when officers are caught misusing confidential databases for personal stalking, they are rarely prosecuted seriously.
- The “deep state” concept describes a defense and national security apparatus that is effectively self-governing, with virtually no accountability or checks and balances.
- Private security firms, often staffed by former government agents, can conduct illegal operations with little scrutiny due to connections and the inability to be investigated by Freedom of Information Act (FOIA) requests.
- Continuity of Personnel and Tactics: There’s a strong indication of overlapping personnel and methodologies between government agencies and private security firms.
- Private investigators, often former agents or cops, are readily available for “mercenary work,” which can include slander and stalking for wealthy clients.
- Emails exposed by Barrett Brown revealed collusion between corporate spies and government agents to target activists and journalists.
In essence, historical instances demonstrate that the tactics attributed to “gang stalking” are not new or imaginary, but rather have a documented history of use by state and private actors, giving a framework for understanding contemporary claims.
The purpose of “disruption” operations, also referred to as “gang stalking,” “organized stalking,” “harassment,” or “Zersetzung,” is multifaceted and generally aims to undermine, intimidate, terrorize, and discredit targets.
Here are the key purposes and motivations behind these operations as described in the sources:
- To silence or “switch off” opponents and critics:
- In the context of East Germany’s Stasi (secret police), “Zersetzung” (corrosion or undermining) aimed to “switch off” regime opponents by disrupting their private or family lives. The tactics were intended to make victims believe they were “going mad,” potentially leading to breakdowns or suicide, while allowing the state to deny responsibility.
- Movie producer Harvey Weinstein allegedly employed private investigation firms to silence his sex abuse victims through spying and intimidation. This campaign ultimately aimed to track and silence his accusers.
- The Koch brothers reportedly hired private investigators to discredit reporting about them, attempting to “plant misinformation” and “dig for dirt” on a reporter; if no genuine dirt was found, the intent was to “create it”. This was a classic case of attacking the messenger.
- The aim of Russia’s harassment of Western diplomats, which uses similar tactics, is to “short-tour” diplomats so they leave their posts early.
- The overall purpose is to demoralize and intimidate their targets.
- To maintain deniability and avoid accountability:
- Stasi tactics like “Zersetzung” were favored because they were “softer” methods of torture, offering deniability and political safety compared to overt persecution, which was important for maintaining international respectability.
- The CIA does nothing it cannot deny, structuring programs and operations to ensure deniability and avoid Congressional accountability for criminal actions.
- Corporations and government agencies can delegate “dirty work” to private firms through contracting and subcontracting, further obscuring responsibility.
- The deniability inherent in these tactics makes it difficult to capture convincing video evidence or other forensic proof.
- To instill fear and psychological distress:
- Tactics like moving personal items, opening windows, setting alarms, or even sending vibrators to a target’s wife were designed to make victims feel like they were “going mad”.
- “Gaslighting” is a specific counterintelligence method aimed at causing the target to question their own memory and sanity, and to give others the impression of mental instability.
- The goal is to terrorize individuals and apply “psychological torture”.
- To control and manipulate perceptions, including public discourse:
- Spreading disinformation is a core element of organized stalking crimes, with many online “gang stalking” websites being intentionally vague and non-credible, designed to give the impression of “paranoia and stupidity” and discredit legitimate claims. This is meant to undermine legitimate accounts by victims.
- The use of “persona management” systems allows one user to control multiple online identities to create the appearance of grassroots support or opposition.
- This is part of a broader effort to “suppress” and “marginalize” criticisms and allegations about corruption in the surveillance and policing business.
- In the case of the Fentanyl flyers, the “staged” incident appeared to be an attempt to discredit the tactical advice (like spreading flyers) from websites fighting gang stalking by associating it with a “ridiculous disinformation website”.
- To gain and maintain power and impunity for state and private actors:
- These operations allow those with security industry connections to “destroy someone without a significant risk of physical, legal, or political consequences”.
- They enable the “de facto extra-legal power” wielded by intelligence and law enforcement agencies.
- The “deep state” operates with “virtually no accountability, transparency, or checks and balances”, allowing for widespread abuses of power.
- They serve as “enforcers – ‘goon squads’ – for corporations, the political establishment, and for other members of the security industry,” often for “mercenary reasons”.
- To punish or retaliate against individuals:
- The FBI’s COINTELPRO operations notoriously aimed to “discredit” and “neutralize” dissident groups, including attempts to pressure Martin Luther King, Jr. to kill himself.
- Journalist Barrett Brown’s rearrest was presumably motivated by his exposure of criminality by intelligence agencies and private firms, an act of “retribution” for his efforts.
- The Washington state case involved a police officer who was sued for cyberstalking and using police resources to “intimidate and keep tabs on” a woman and her family.
- The Ventura County case suggests police units used militarized tactics to “terrorize the defendants for daring to suggest that the firefighters might have been at least partly to blame”.
In essence, “disruption operations” are a set of covert, often illegal, and psychologically manipulative tactics employed by state and private security entities to control, neutralize, or punish individuals or groups perceived as threats or inconveniences, while maintaining plausible deniability and avoiding public accountability.
The Streisand Effect refers to the unintended consequence of an attempt to hide, remove, or censor information, which instead draws greater attention to that information. The more someone tries to suppress something, the more public attention it gains.
In the context of “disruption” operations, also known as “organized stalking” or “gang stalking,” the Streisand Effect is a strategic consideration for the victims and a risk for the perpetrators.
Here’s how it applies:
- Perpetrators’ Desire for Low Profile: Individuals and entities involved in illegal harassment and spying, such as quasi-governmental “Law Enforcement Intelligence Units (LEIUs),” “parasitic security contractors” like “Surveillance Role Players (SRPs),” and vigilantes associated with corrupt police, do not want to risk calling attention to their crimes by publicly challenging individuals who distribute flyers. Criminals, even those with government connections, prefer to keep a low profile.
- Victim’s Tactic of Exposure: Victims of illegal harassment are encouraged to use the tactic of leafleting (distributing flyers) to expose the crimes. These flyers can directly inform fellow citizens about illegal spying and stalking by private investigators, vigilantes, and corrupt law enforcement personnel. This public exposure is “extremely disruptive” for the perpetrators.
- Generating Attention: Distributing flyers can lead to inquiries to local authorities, which can, in turn, result in published news reports and investigations by the media and government. This widespread attention is precisely what those perpetrating the secret harassment wish to avoid, as it could expose their activities and lead to accountability.
- Naming Perpetrators: If victims know the identity of a person or business involved in the harassment, they can consider “burning” the perpetrator by exposing their identity in the flyers. While there’s a theoretical risk of libel accusations, the stalkers are unlikely to want a public fight about organized stalking allegations, fearing the Streisand Effect. No “cowards, thugs, and traitors” will want their names or businesses publicly associated with stalking.
Based on the sources, SELF is a non-linear organizing framework and an acronym representing four interactive key aspects of recovery from traumatic experiences. It functions as a cognitive-behavioral therapeutic approach designed to facilitate movement towards healing.
Here’s a breakdown of what SELF is and its purpose:
- Acronym and Key Domains:
- Safety – focused on achieving safety in oneself, relationships, and the environment.
- Emotional management – involves identifying levels of various emotions and modulating them in response to memories, people, and events.
- Loss – addresses the process of feeling grief, dealing with personal losses, and recognizing that all change inherently involves loss.
- Future – encourages trying out new roles, ways of relating, and behaving as a survivor to ensure personal safety and help others.
- Purpose and Utility:
- A Compass for Healing: SELF serves as a “compass” to explore these four key domains of healing.
- Shared, Non-Technical Language: It provides clients, their families, and staff with a shared, non-technical, and non-pejorative language, allowing them to view the broader recovery process in perspective. This accessible language helps demystify confusing or insulting clinical and psychological terminology for clients and line-staff, while still focusing on problematic aspects of pathological adjustment.
- Parallel Process Application: A significant utility of SELF is its ability to be simultaneously employed in a “parallel process” manner. This means it can be used to address problems that arise within the treatment setting, such as issues between staff and clients, among staff members themselves, or between staff and administration.
- Organizational Problem-Solving: When applied to organizational dilemmas like staff splitting, poor morale, rule infractions, administrative withdrawal, helplessness, and misguided leadership, SELF can assist a stressed organization in conceptualizing its current challenges and moving towards a better future through complex decision-making and conflict resolution.
- Integration within the Sanctuary Model:
- The Sanctuary Model is not a specific treatment intervention, but rather an “operating system” for a trauma-informed organization. SELF is a conceptual tool for organizing treatment within this model.
- It integrates long-established good organizational practices with the newer sciences of trauma and attachment studies. The Seven Commitments (e.g., non-violence, emotional intelligence, social learning, open communication, democracy, social responsibility, growth and change) and the Sanctuary Toolkit are also vital elements of this “organizational spacesuit” that allows for exploring new, healthier organizational states.
- Training in the Sanctuary Model, through the Sanctuary Institute, includes developing an understanding of SELF as a core tool. Core Teams, responsible for implementing the Sanctuary Model, teach everyone about SELF, trauma theory, the Seven Commitments, and the Sanctuary Toolkit.
The Sanctuary Model was written by Sandra L. Bloom.
It was originally developed by Sandra L. Bloom during the period of 1980-2001, specifically in a short-term, acute inpatient psychiatric setting for adults who had experienced trauma as children. Sandra L. Bloom is affiliated with Drexel University and has numerous publications and citations related to this work. Further development of the Sanctuary Model was also supported by an NIMH research grant through the Jewish Board of Family and Children’s Services in New York, and the current training and implementation process is a joint achievement of Bloom and the Andrus Children’s Centre in Yonkers, New York.
Project PM was an online crowd-sourced analysis initiative organized by journalist and activist Barrett Brown in 2009. Its primary purpose was to sort, analyze, and share a huge amount of information from hacked emails belonging to private security firms, specifically HBGary and Stratfor. Brown himself was not involved in the hacking of these emails but took on the painstaking work of collating and connecting the dots once the emails were posted on a BitTorrent site.
Here’s a more detailed breakdown of Project PM:
- Purpose and Methodology:
- Crowd-Sourced Investigation: Brown rallied approximately 100 volunteers to trawl through and make sense of the tens of thousands of emails from HBGary and millions from Stratfor. The hackers initially didn’t want to dump the HBGary emails, but Brown recognized their importance and organized the effort to analyze them.
- Exposing the “Shadowy Ecosystem”: Project PM aimed to expose the “slimy ecosystem” of mercenary spooks who performed counterintelligence “dirty work” for powerful corporate clients like Bank of America and the U.S. Chamber of Commerce. It sought to “untangle a web of connections between the US government, corporations, lobbyists and a shadowy group of private military and information security consultants”.
- Revealing Corporate-State Partnerships: The HBGary cache, analyzed by Project PM, offered “one of the fullest looks ever at how corporate-state partnerships were targeting groups they considered subversive or inimical to the interests of corporate America“. This also included intelligence contractors working with local and federal law enforcement, for instance, spying on “Occupy Austin” for the Texas State Troopers.
- Battling Disinformation: The emails revealed schemes to spread disinformation, including plots to exploit online “personas” or “sock puppets” to create the appearance of grassroots support or opposition for certain policies. Project PM’s work implicitly countered such tactics by providing factual analysis of these operations.
- Expanding Public Understanding: Brown’s goal with Project PM was to “expand these peepholes” into the world of private intelligence and cybersecurity contracting, a $56 billion industry that consumes 70 percent of the U.S. intelligence budget.
- Key Revelations:
- Project PM helped expose “Team Themis,” a consortium of private intelligence firms (HBGary, Palantir Technologies, Berico Technologies, and Endgame Systems) organized by the law firm Hunton and Williams. This group’s objective was to discredit critics of the Chamber of Commerce, WikiLeaks, and journalist Glenn Greenwald through tactics like creating false documents and “fake insider personas”.
- It also revealed connections between these private counterintelligence operations and the U.S. Department of Justice (DOJ), which had reportedly made introductions between Bank of America and Hunton and Williams to address WikiLeaks’ claims.
- The project illuminated the practice of “persona management” systems for government agencies, like the U.S. Air Force, to control multiple online identities and manipulate social media discourse.
- Consequences and Legacy:
- Brown’s efforts with Project PM, and his subsequent reporting on the exposed criminality, led to him being targeted by the Department of Justice, which pursued charges against him in “retaliation for my efforts to keep the story alive”. The FBI was particularly concerned with his investigations into their “criminal allies, such as HBGary Federal, and the site on which we compiled our research, echelon2.org”.
- While Project PM “as such” is not being revived, Barrett Brown and his team are developing “Pursuance,” a new system designed to continue much of the same work of documenting the intelligence sector, both private and public, aiming to provide a more secure and effective platform for activists and journalists to expose corruption. This new system seeks to address the “fatal flaws” of previous decentralized efforts like Anonymous, such as a lack of mechanisms for settling disagreements.
Pursuance is a new system being developed by journalist and activist Barrett Brown and his team. It functions as open-source encrypted software designed to enable individuals to form networks for sharing information and collaborating on common goals.
The primary purpose of Pursuance is to continue the work of documenting the intelligence sector, both private and public, which was previously undertaken by Brown’s earlier initiative, Project PM.
Key aspects of Pursuance’s purpose include:
- Secure Collaboration and Information Sharing: It is being designed from the ground up as a platform particularly well-suited for activists and journalists who anticipate attempts by government and corporate operatives to infiltrate and subvert their projects. The system aims to provide a more secure and effective platform for exposing corruption.
- Addressing Flaws of Previous Movements: Pursuance seeks to remedy the “fatal flaws” found in earlier decentralized efforts, such as the Anonymous movement. These flaws included a lack of clear mechanisms for settling disagreements and situations where some individuals controlled the mediums (like IRC servers) where important work was conducted.
- Facilitating Investigative Journalism and Activism: The project aims to allow Brown and others to get back to the work of more journalism, more collaborations, and providing tools to “keep those who view investigative journalism as threatening locked out of the process”.
- Structured Civic Engagement: It is envisioned as a mechanism for conducting civic affairs in a way that provides everyone with “the same clearly-defined rights to operate, to invent, to rise according to their talents and dedication”.
In essence, Pursuance is Brown’s evolution of Project PM, created to provide a more robust, secure, and organized framework for citizens to collectively investigate and expose the complex and often illicit activities of the intelligence and security industry.
Pursuance is an open-source encrypted software system being developed by journalist and activist Barrett Brown and his team. Its core purpose is to enable individuals to form networks for sharing information and collaborating on common goals.
Specifically, Pursuance is designed to:
- Continue Investigative Work: It aims to continue much of the same work of documenting the intelligence sector, both private and public, which was initiated by Brown’s previous project, Project PM.
- Facilitate Secure Collaboration: The system is designed as a platform specifically well-suited for activists and journalists who anticipate attempts by government and corporate operatives to infiltrate and subvert their projects. This includes providing a more secure and effective platform for exposing corruption.
- Address Previous Flaws: Pursuance seeks to remedy “fatal flaws” found in earlier decentralized movements like Anonymous. These flaws included a lack of clear mechanisms for settling disagreements and situations where certain individuals controlled the mediums (such as IRC servers) where important work was conducted.
- Promote Investigative Journalism: It is intended to allow Brown and others to “get back to the work” of more journalism and more collaborations, offering a suite of tools to “keep those who view investigative journalism as threatening locked out of the process”.
- Structure Civic Engagement: Pursuance is envisioned as a mechanism for conducting civic affairs in a way that ensures everyone has “the same clearly-defined rights to operate, to invent, to rise according to their talents and dedication”.
In essence, Pursuance aims to be a robust, secure, and organized framework for citizens to collectively investigate and expose the complex and often illicit activities within the intelligence and security industries.
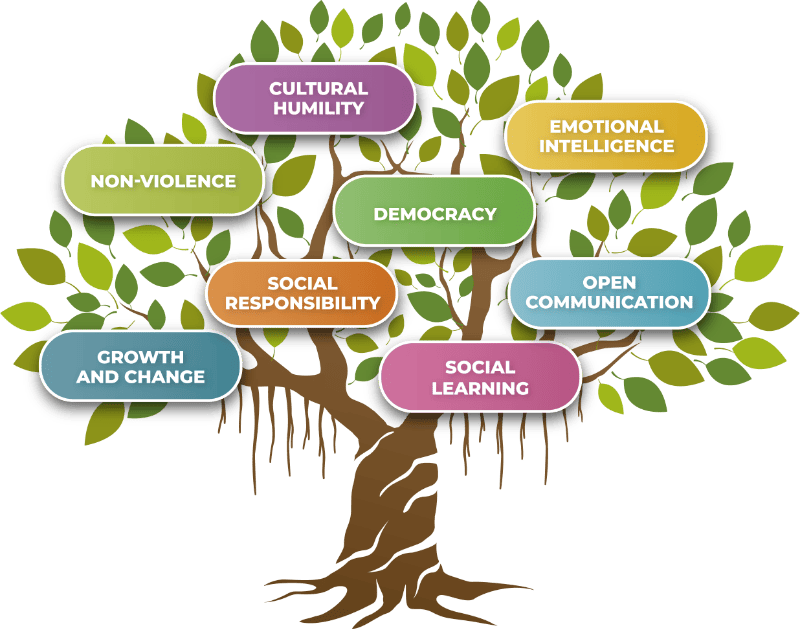
The Seven Commitments are a set of guiding principles and basic structural elements for the implementation of the Sanctuary Model. They are designed to structure the organizational norms that define an organization’s culture.
Within the Sanctuary Model, which is a theory-based, trauma-informed, evidence-supported, whole-culture approach for creating or changing an organizational culture, the Seven Commitments help to establish a cohesive context for healing from psychological and social traumatic experiences. They aim to counteract the “biological, affective, cognitive, social and existential wounds” suffered by victims of trauma and extended exposure to adversity. These commitments apply to everyone within an organization, including staff, clients, and the wider community. Organizational leaders, from the board of directors to staff at all levels, must be fully committed to these principles for the Sanctuary Model to be effective.
Here are the Seven Commitments:
- Commitment to non-violence: This involves building safety skills, fostering trust, and inspiring a commitment to broader socio-political change, while reducing systemic violence, including physical, verbal, and emotional forms.
- Commitment to emotional intelligence: This commitment aims to teach emotional management skills and expand awareness of problematic cognitive-behavioral patterns and how to change them.
- Commitment to social learning: It focuses on building cognitive skills, improving learning and decisions, and creating and sustaining a learning organization.
- Commitment to open communication: This is about overcoming barriers to healthy communication, discussing difficult topics, increasing transparency, developing conflict management skills, and reinforcing healthy boundaries.
- Commitment to democracy: This involves developing civic skills of self-control and self-discipline, learning to exercise healthy authority and leadership, developing participatory skills, overcoming helplessness, and honoring the voices of self and others.
- Commitment to social responsibility: The goal here is to harness the energy of revenge by rebuilding social connection skills, establishing healthy attachment relationships, and transforming vengeance into social justice.
- Commitment to growth and change: This entails working through loss, recognizing that all change involves loss, and envisioning, skillfully planning for, and being guided by a different and better future.
The Seven Commitments, along with SELF and the Sanctuary Toolkit, are considered vital elements of the “organizational spacesuit” that allows an organization to explore unknown territory while maintaining safety during a change process.